The information security plan describes how companies implement information security solutions, policies and controls. The information security plan is developed considering all the IT resources depending on the security levels achieved and the pending aspects. Besides, an information security plan should focus on the actions required to achieve higher levels of security. It is very important to define its scope. According to logical security experts, the scope helps to define priorities and actions depending on the IT resources at reach.
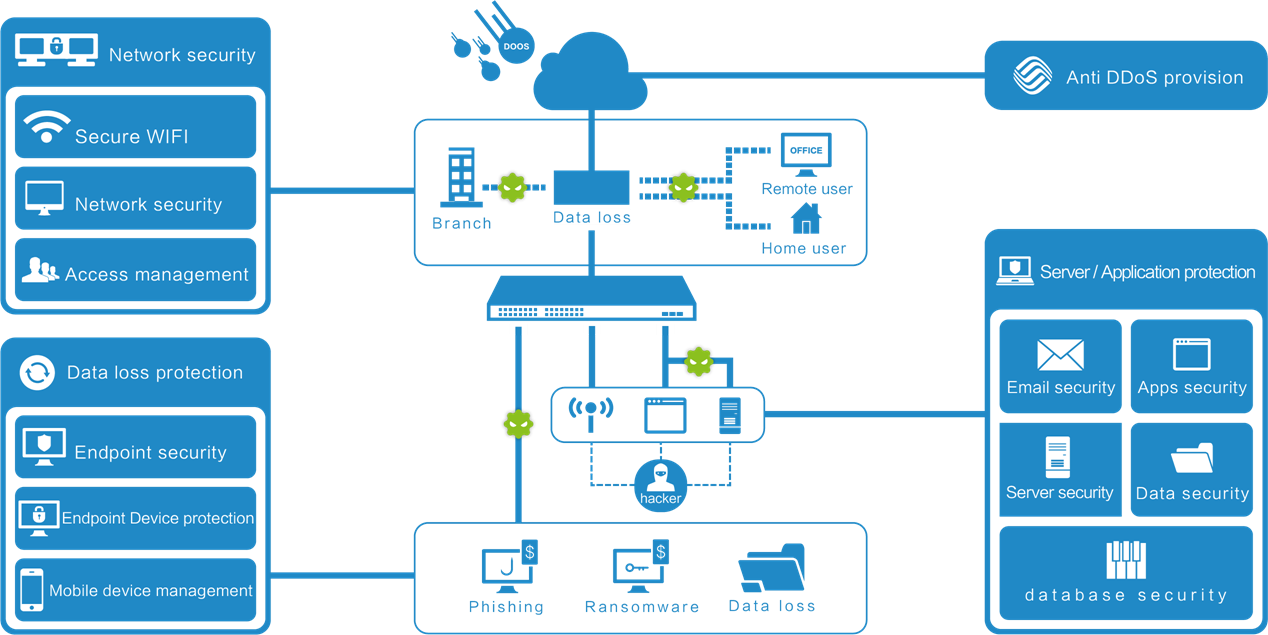
Physical security and logical security are two basic aspects within an information security plan and are vital for the correct security implementation in the company. Details on each these services are explained below.
Logical Security
Most of information security plans begin with logical security. Logical security implicates logical security policies and logical security solutions for any enterprise.
Logical Security Solutions
There is a wide range of logical security solutions sold by multiple logical security companies in the market. Enterprise logical security solutions are necessary to prevent, detect and recover from a security breach incident; moreover, having it in place can prevent lot of data breach incidents and unauthorized access to company’s resources. Logical security policies and network perimeter security systems should work synchronously and our logical security solutions help you create logical barriers that protect your company’s information.
As per the experience of logical security company experts, enterprises normally only rely on network perimeter security systems and antivirus tools to defend IT infrastructure against threats. Our logical security services ensure defense against advanced attacks by going beyond existing network perimeter security solutions. So it is very essential to have an IT security plan that includes perimeter & logical security.
Logical Security Policies
The primary objectives of the implementation of logical security policies is providing guidance and helping to the management, in accordance with business requirements and security standards. Logical security policies represent business goals and commitment to data security and should be communicated to all employees of the company.
Logical security policies define the resources that must be protected and it’s worth noting that logical security itself doesn’t define how the IT resources are protected. This is defined through logical security solutions. For each policy there may exist several logical security solutions.
Since logical security policies can affect all employees, it is important to make sure to have authorization for their implementation. Logical security polices must be created with the help of experts with experience; in addition, these processes have to be approved by the company’s management. Policies for incident management, data backup and protection of personal data form an integral part of logical security.
Network Perimeter Security
The next step to create an information security plan has to do with the implementation of a network perimeter security system. No matter the size or industrial sector, all companies use some variant of network perimeter security system to protect their resources against threat actors. Network perimeter security is responsible for the security of the company’s IT resources against external threats such as viruses, worms, Trojans, denial of service (DDoS) attacks, data destruction/theft, and so on.
Formerly, network perimeter security only incorporated firewall, but the current market for perimeter security has changed a lot, so network perimeter security systems have also incorporated Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). Experts in the implementation of network perimeter security explain that systems should inspect application protocols and content, besides using advanced techniques to identify unknown threats.
Our Network perimeter security solutions provide protection at two different levels:
- At network level: The network perimeter security system provides protection against threats like hackers, intrusions or theft of information.
- At content level: Perimeter security system for content provides protection against threats such as malware, phishing, spam and inappropriate web content.
These characteristics have forced the consolidation of the IT security plan, taking perimeter security to the next level. Also the way in which threats are evolving in recent years has led perimeter security companies to focus on the development of next generation products.
Users’ Identification and Authentication
Identification and authentication of users is an important part of the IT security plan for companies. Network perimeter security systems should identify and authenticate any user. The allocation of rights and privileges in a network perimeter security system are controlled through an authorization process, which determines the profile of each user.
Network perimeter security solutions guarantee access to authorized users and prevent unauthorized access to IT resources. Our perimeter security experts take into considerations the following aspects during the implementation of network perimeter security:
- Logical security policies for classification, authorization and distribution of information.
- The standards and company’s obligations regarding protection of information access.
- Perimeter security audit processes to verify access controls.
- Maintaining access records for network perimeter security system.
- The procedures for user identification and verification of access of each user.
- Perimeter security solutions covers all phases of the life cycle of user access, from the initial registration of new users to the cancellation of the registration of users who do not require access to IT resources.
- System and authentication method used by the network perimeter security systems for information security.
- Using advance network perimeter security solutions for access control, such as bio-metrics, smart cards, etc.
- Define IT resources, which must be protected with the help of network perimeter security.
- Authorization processes and methodology used by network perimeter security system.
According to information security plan experts, the reviewing process of user access rights is very important after any change. Our network perimeter security solutions help you prevent unauthorized modification, destruction and loss of data belonging to access control system.
Physical Security Solutions
An information security plan is not completed without the implementation of physical security. The physical security is designed to achieve efficient management of security, and these solutions must comply with the highest standards established by law enforcement and the company itself.
The physical security solutions when implemented as a part of information security plan are intended to prevent unauthorized physical access, damage and interference to the IT infrastructure and company’s confidential information. Physical security forms an integral part of the IT security solutions and the success of any information security plan.
IT departments and other areas involved in data management can implement physical security solutions. The information security plan must first identify all areas inside the company, the areas with specific security requirements and, on this basis, limited, restricted and strategic areas must be declared to implement physical security solutions in each area described.
Physical security solutions considered in the information security plan create a physical barrier around the areas of information management; nonetheless, some solutions use multiple barriers to provide additional protection. Companies must periodically do IT security plan audit to determine the required actions to achieve the business goals.
The protection of the IT infrastructure and business devices form an integral part of physical security solutions and are needed to reduce the physical threats of unauthorized access to information and risks of theft or damage. IT security plan must take into account the actions needed to fill gaps in security and for correcting errors.
According to IT security plan experts, these tools ensure protection against power failures, information leakage or interception, and cable protection. According to information security plan consultants, physical damages potentially caused by natural disasters (such as fires, floods, earthquakes, explosions, among others) should be considered while designing the comprehensive IT security plan.
Implementing an information security plan is a vital step for any company. The International Institute of Cyber Security (IICS) is an organization specializing in logical security services; our information security plan is suitable with any security system and security management protocol. Besides, our IT security plan is really easy to implement and ensures its compliance.
Our information security plan covers logical, physical and network perimeter security solutions. Our information security plan specialists have collaborated with the most important companies in private and public sectors worldwide; with expertise security centers in Mexico, US, and India, the International Institute of Cyber Security delivers the best solutions, services for companies. We have a partner program that recognizes the effort and investment of strategic allies, offering logical and network perimeter security solutions to achieve sustainable and mutually beneficial business. Our partners / partners program is available in Australia, UK, Dubai, Qatar, Sri-Lanka, Saudi Arabia, Thailand, Malaysia, Singapore, Nigeria, Kenya & South Africa.
