Global perspective of data security companies puts five essential aspects for any business data security training: integrity, confidentiality, availability, auditability and non-repudiation. Data security has become a critical matter for small and medium-sized companies in countries like Australia, UK, Dubai, Sri-Lanka, Saudi Arabia, Thailand, Malaysia, Singapore, Nigeria, Kenya & South Africa. Data security training not only helps to improve a company’s IT resources security, but it also ensure that technology resources will be able to handle any contingencies that may interrupt the organization’s growth.
Any company can easily implement a security framework, such as data security management systems, with the help of business data security training.
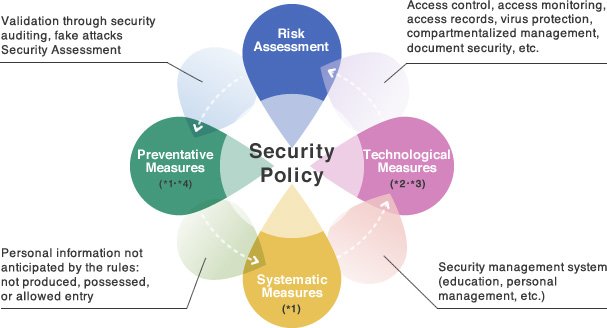
Our data security course teaches the implementation of these security frameworks. Data security management system covers different areas, such as security plans, data security policies, and quality assurance, among others. The complete implementation of a data security management system consists of three processes:
- Planning
- Implementation
- Verification & Updating
According to data security course experts associated with enterprise data security companies, a data security training covers several functions, including visibility over the current state of TI resources, data security controls and enterprise data security specialization, which could be applied to take relevant decisions while deciding the company’s strategies. The following are the phases covered during our data security course:
Planning of the data security management system
This process involves the data security management system architecture. Data security company experts mention that this process allows establishing data security training policies and accomplish the company’s data security objectives.
The first step in the planning process is to determine the security requirements for each specific case.
Determine the security requirements
Security requirements are determined through the implementation of a data security course and are an important part of the data security management system design. Security risk analysis covered during the course helps in calculating the potential impacts of risks, their probability of occurrence and identification of IT resources to protect.
Our data security course focuses on following process:
- Defining IT resources.
- Identifying and evaluating threats and vulnerabilities along with their priorities.
Besides, two aspects can distinguish our data security course:
- Our data security course teaches risk assessment, to determine which systems can be affected by threats and establishing risk priorities and impacts.
- Our data security course allows the identification, selection, approval and risks management and data security controls to eliminate or reduce risks. As per data security industry standards the course helps to mitigate the threat’s impact and during the recovery process.
Thus our data security course determines the security requirements and covers the following processes:
Define IT resources
IT resource definition includes the determination of all the IT resources that must be protected, their value and classifications according to the company’s priorities. According to the data security company experts, a good definition of IT resource should include any aspect that makes more precise its description and location, types of technology, people that operate it, among others.
Before taking a personalized data security course, companies must perform the definition of IT resources taking into account aspects such as the function performed, costs and effort value. Data security company consultants, mention that this process helps in determining the critical IT resources and the risks to which they are exposed.
According to the experience of data security company experts there is a trend to declare IT resources as critical even if they’re not actually that important. The company should focus on this while taking the data security course to avoid problems in the future.
Security risks identification and evaluation
Companies can identify security risks in IT resources with the help of a data security course, as it is an important part of the data security management system architecture. On the other hand, risk analysis involves the examination of each threat; this estimation determines the changes of an attack and helps choosing the best security controls that should be implemented.
Companies typically implement some option of data security training. According to data security company specialists, it is necessary to assess the effectiveness of existing data security training, on the basis of results from risk analysis. This will help businesses to guide and implement data security training with more effectiveness or to take help from an data security company to protect their IT resources.
Selection of data security controls
Companies should select data security controls based on the risk analysis, the criteria for the risk acceptance, the options for resolving risks, and to meet the security standards. Companies can identify security controls during personalized data security course. Security controls are an integral part of any business data security training and of the data security management system architecture. Implementation of a data security management system can be achieved by implementing a suitable set of controls, which include policies, procedures, processes and trainings.
Experts with experience in the implementation of data security management system must review selection of security controls during data security course or by heads of companies that have the power to enforce them. As per the data security company experts, data security training and procedures are the first step in protecting IT resources. Security controls must be implemented using procedures and trainings that ensure their compliance. Solutions covered during our data security training are classified according to their origin:
- Administrative
- Physical or logical security
- Operational security
- Educational
At the same time, the methodology of the business data security training can be:
- Prevention
- Detection
- Recovery
In the case that a business does not have expertise to implement data security trainings, it could establish contacts with enterprise data security companies or external groups, including appropriate authorities, to keep up with the industry trends, monitor standards and methods of evaluation.
Implementation of data security management system
The process of implementation of the data security management system includes management of risks identified through the application of data security trainings and controls. This process ensures that the company employees the knowledge and skills, through data security training. According to the data security course professor, companies should implement training programs and courses that cover the following aspects:
- The employees should understand the importance of the data security management system for the organization, with the help of the data security training.
- The data security training must ensure the dissemination of knowledge and understanding of the security policies that are implemented.
- The course should train the users in procedures and solutions that will be implemented.
- The employees must be aware of the roles they need to fulfill within the data security management system after taking the course.
- With the help of data security training, employees must understand the procedures and controls that are required to detect and provide timely response to the security incidents.
For the successful implementation of data security management system, companies must ensure the implementation of all controls, including policies, procedures, processes, trainings and development of employee’s skills.
Verifying and updating data security management system
The process of verification of data security management system includes verification of the performance, the effectiveness of the ISMS and the periodic verification of the residual risks. According to the data security company experts, businesses must do periodic internal/external audit to achieve their business objective.
The process of updating the data security management system includes making changes based on the results of the verification process to ensure maximum performance of the data security management system. This process usually runs in parallel with the process of verification, thus is also responsible for the maintenance of the system. As per experience of the data security course trainers, during the implementation of this process modification of the security controls or implementing new business data security trainings o solutions may be required. Thus companies must evaluate new risks and provide training to staff about the changes or about new solutions.
The implementation of data security management system is an important step in the field of data security. The International Institute of Cyber Security (IICS) is a data security company and has a team of experts in the implementation of data security management systems. In IICS, our data security course experts have years of experience working with private companies and public organizations in several countries. With data security course centers in Mexico, USA and India, the International Institute of Cyber Security (IICS) offers solutions, services, and data security courses. We have a partner program that recognizes the effort and investment of strategic allies, offering online courses, classroom courses, services and solutions to achieve sustainable and mutually beneficial business. Our partners / partners program is available in Australia, UK, Dubai, Qatar, Sri-Lanka, Saudi Arabia, Thailand, Malaysia, Singapore, Nigeria, Kenya & South Africa.
