Maintaining today’s computer networks is like a betting game. If you are doing business on the Internet, you manage web applications that keep confidential information or you are a financial services or healthcare services company; vulnerability assessment should be your first concern. In countries such as India, Dubai, Sri-Lanka, Saudi Arabia, Thailand, Malaysia, Nigeria, Kenya and South Africa IT security risk assessment is not given much of importance. However companies are dependent on technology to drive their business operations, thus it is crucial for companies to do IT security risk assessment and secure themselves.
Vulnerability is considered a risk and is a characteristic of an information asset. IT vulnerabilities can be detected with IT security assessment. When an IT risk materializes and there is a vulnerability that can be exploited, there is a possibility of loss of confidentiality, integrity, availability and authenticity of business data. Vulnerability assessment experts around the world discover hundreds of new vulnerabilities every year and release new security patches every month. For these reasons, it is necessary for any company or organization to do IT security risk assessment that will allow them to know their IT systems vulnerabilities.

IT security risk assessment services must identify all the security risks and ensure peace of mind for all the company’s executives. Vulnerability assessment and network vulnerability testing form an integral part of IT security assessment. It provides much valuable information about the company’s exposure to risks. These risks and vulnerabilities enable a company or organization to deal with an eventual materialization of IT risks.
With the clear identification of IT risks, companies can implement preventive and corrective solutions with the help of a professional IT security risk assessment company. Preventive and corrective solutions must maintain a balance between the cost that the resolution of vulnerability has, the value of the information asset for the company and the level of criticality of the vulnerability. Implementing vulnerability assessment and network vulnerability testing along with corrective measures gives confidence to your customers about their data and gives your company a competitive advantage.
IT security risk assessment ensures compliance with national or international standards for each industry. In some industries, it is necessary to have a proper network vulnerability testing plan. In industries such as healthcare & finance, that handle critical and high-risk equipment, periodic IT security risk assessment helps to strengthen the technology environment by proactively addressing potential threats. Vulnerability assessment services can be classified as internal vulnerability assessment and external vulnerability assessment.
External vulnerability assessment service
The external vulnerability assessment service assesses the technology infrastructure of the company from the perspective of a hacker through the Internet. The service only requires IP address of the network, business applications and nothing needs to be installed. During the vulnerability assessment, professionals should focus on new types of external attacks, zero-day vulnerabilities and their methodology to do assessment of known vulnerabilities.
Internal vulnerability assessment service
The internal vulnerability assessment service assesses the security profile of the company from the perspective of an insider, employee or someone with access to corporate systems and networks. Normally the service is personalized as per company’s requirements because each company has different types of networks and internal applications. During the vulnerability assessment professionals must simulate an external hacker via the Internet or an insider with normal privileges. They should also focus on new types of internal attacks, network vulnerability testing, zero-day vulnerabilities and methodology to do network assessment of known vulnerabilities.
Advantages of our vulnerability assessment services
- If you are a large corporation or a small business, you will find our services very easy and efficient.
- Our IT security risk assessment services ensure that complete IT infrastructure (networks, applications and mobile) meets the objectives of security.
- We have specialized infosec experts along with the best techniques and strategies of IT security assessment.
- We do not use traditional methodology used by many IT security assessment companies. We apply our methodical and innovative approach for doing network security testing. We use our own scripts and do code review, along with manual network security testing and use proprietary, commercial, open source tools.
- The deliverables of IT security risk assessment services are reports and corrective recommendations. Vulnerabilities and corrective actions are classified based on the priority of the risks.
- We do IT security risk assessment services as per the international standards.
- Vulnerability assessment service can be performed once or can be a recurring service, to protect IT assets (networks, applications and mobile) against loss and unauthorized access.
- Furthermore we teach how to do IT security assessment to your technical team in real time via vulnerability assessment training. This training would help you to maximize your ability to respond and protect your network against attacks.
Our Vulnerability assessment Methodology (PESA)
Our vulnerability assessment methodology is focused on full protection of resources (networks, applications, mobile devices), which are subjected to internal or external attacks. The methodology is an iterative process, because technology never stops evolving and with new technology new risks for businesses are generated. Our vulnerability assessment methodology also known as PESA; has been structured in different modules.
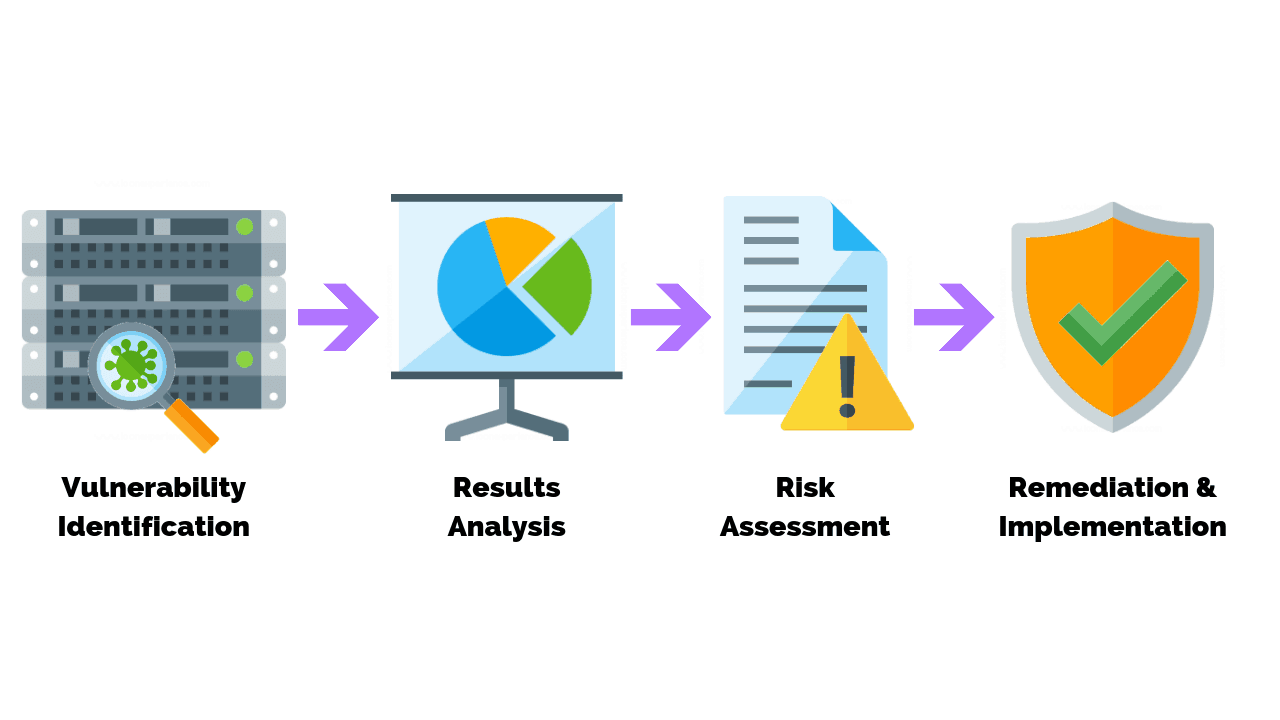
Module: Plan
Much of the successful delivery of our methodology begins to develop in the planning module. In this module we establish the requirements, plans, priorities and we implement the methodology.
Module: Evaluate
In this module we perform analysis of data, networks, applications, databases and mobile devices with vulnerability assessment and network security testing. Following are some of the processes in the evaluation module:
- We do analysis of potential risks at business level and identify physical & logical threats.
- During network security test, we review the configuration of operating systems, enterprise applications; log files and devices that are part of the network architecture.
- We check authentication of users and access control along with monitoring of user activities.
- We do an IT security assessment of services provided by the vendors or by third party to the company
- Review of network security test plans, security policies and contingency plans already in place.
- We use our own scripts, manual network security testing, and make use of proprietary, commercial and open source tools for vulnerability assessment of network, network equipment and mobile devices.
- We use our own scripts, do code review, manual vulnerability assessment, and make use of proprietary & commercial tools for IT security risk assessment of applications and databases. We cover black box and white box testing to find security vulnerabilities.
Module: Secure
In this module we deliver the application assessment, network security testing & contingency plan. We implement security policies with an effective cost-benefit ratio. We work with the client’s team to secure the network architecture, network devices, mobile devices & business applications. We train client’s employees with IT security risk assessment course and vulnerability assessment training.
Module: Audit
The purpose of this module is to verify the implementation and performance of security systems with reassessment. The audit determines whether the security systems safeguard assets and maintain the confidentiality, integrity and availability of the information.
With research centers in Mexico, USA and India, International Institute of Cyber Security delivers tools, services and vulnerability assessment trainings. We have a partner program that recognizes the effort and investment of strategic allies, offering IT security risk assessment services to achieve sustainable and mutually beneficial business. Our partners/partners program is available in Australia, India, UK, Dubai, Qatar, Sri-Lanka, Saudi Arabia, Thailand, Malaysia, Singapore, Nigeria, Kenya & South Africa.
